Build Your Tech Skills with Industry-Focused Courses
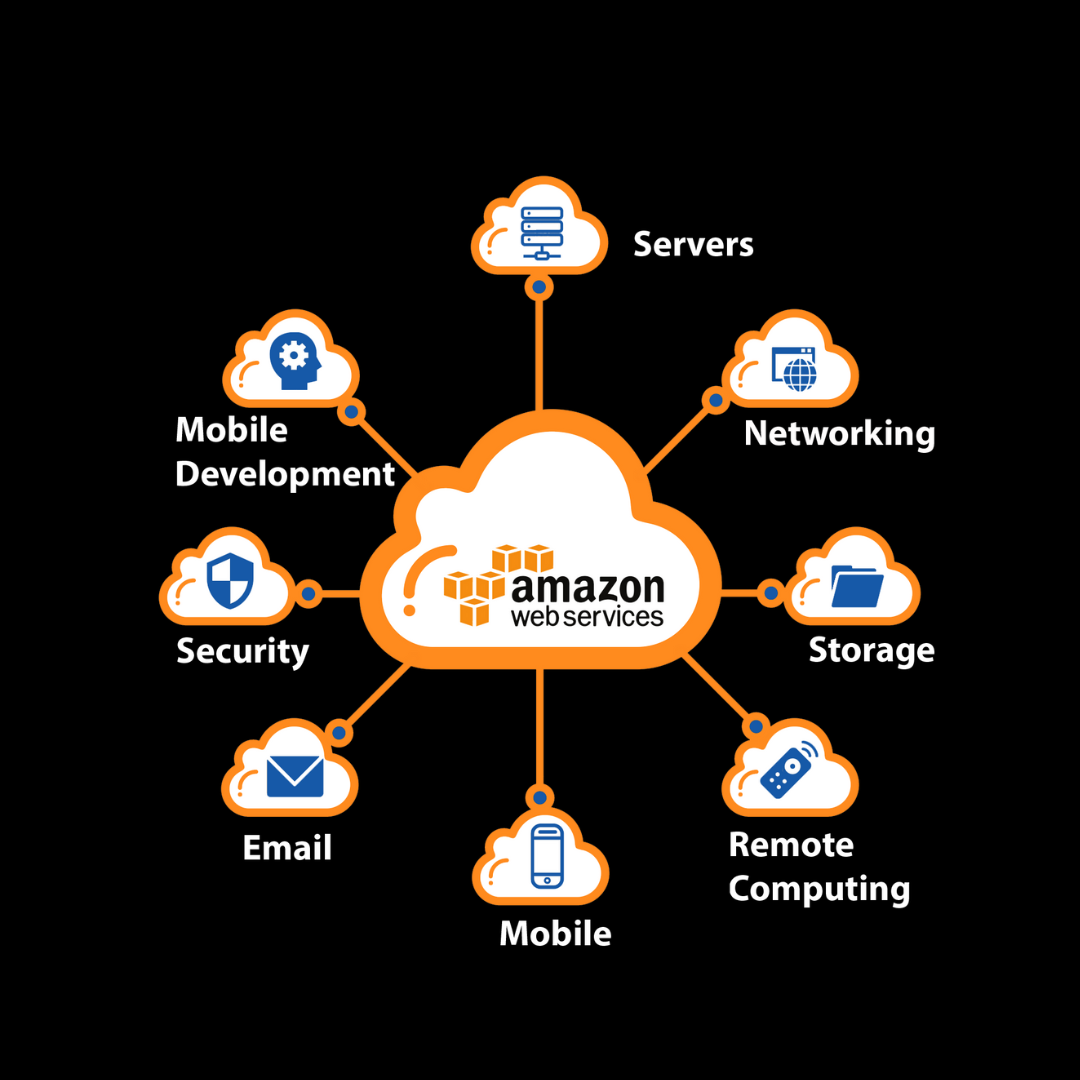
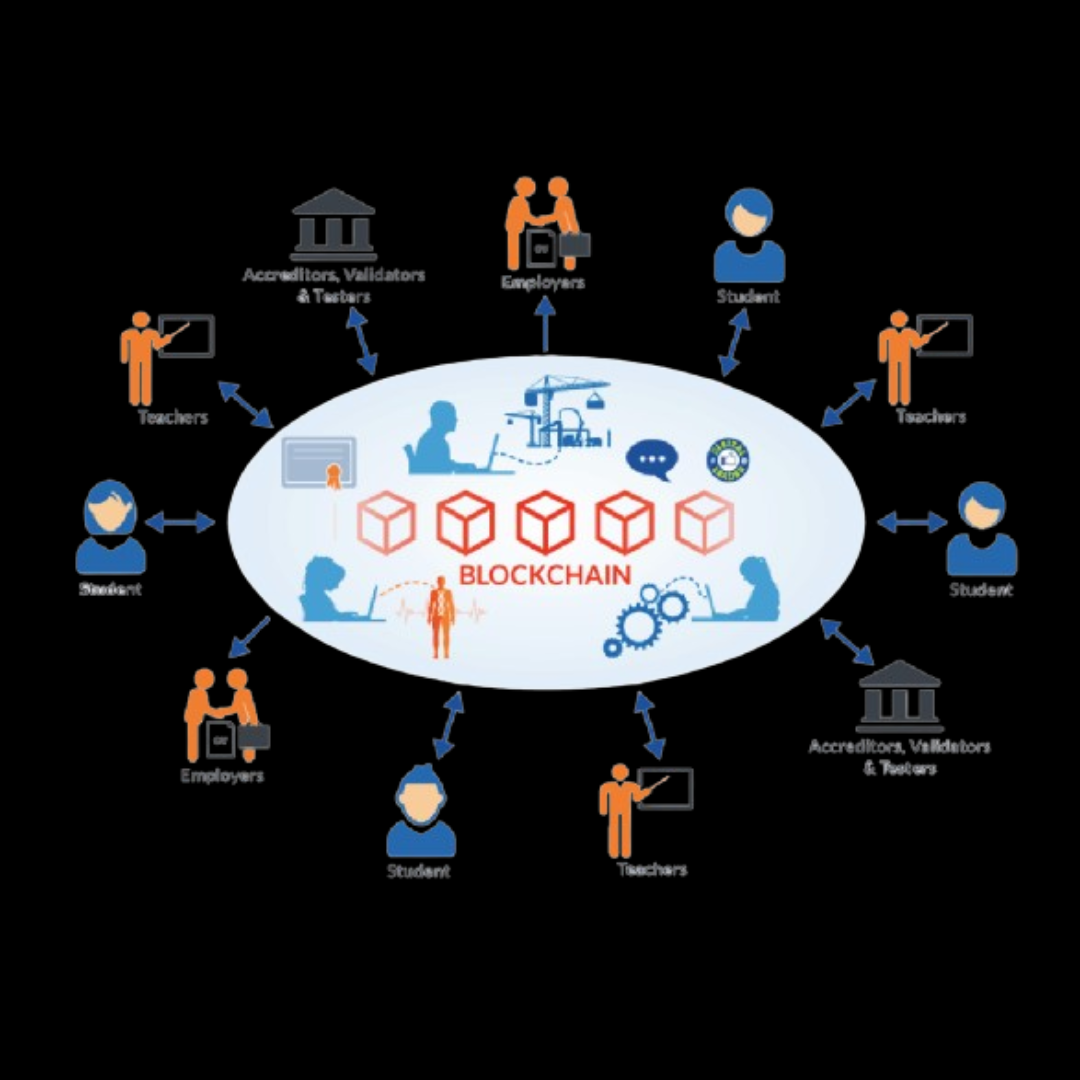
Explore our practical computer courses designed to equip you with real-world skills in programming, web development, cybersecurity, AI, and more. Whether you're starting out or looking to upgrade, our expert-led training helps you stay ahead in today’s tech-driven world.
Course Catalog